'Bad Rabbit' ransomware strikes Ukraine and Russia
A new strain of ransomware emerged today and hit a number of high profile institutions in Russia and Ukraine, such as the Kiev metro system, the Odessa airport, as well as the Russian news agency Interfax and other Russian websites.
"In some of the companies, the work has been completely paralysed - servers and workstations are encrypted," head of Russian cyber-security firm Group-IB, Ilya Sachkov, told the TASS news agency. Two of the affected sites are Interfax and Fontanka.ru.
The attacks are disturbing because attackers quickly infected critical infrastructure, including transportation operators, indicating it was a “well-coordinated” campaign, said Robert Lipovsky, a researcher with cyber firm ESET. More than half the victims were in Russia, followed by Ukraine, Bulgaria, Turkey and Japan, according to ESET.
The cyber-police chief in Ukraine confirmed to the Reuters news agency that Bad Rabbit was the ransomware in question. It bears similarities to the WannaCry and Petya outbreaks earlier this year. However, it is not yet known how far this new malware will be able to spread
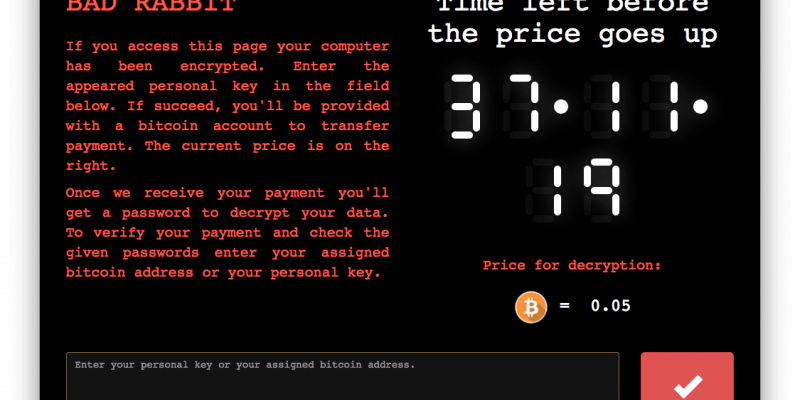
Meanwhile, US officials said they had "received multiple reports of Bad Rabbit ransomware infections in many countries around the world". Bad Rabbit encrypts the contents of a computer and asks for a payment - in this case 0.05 bitcoins, or about $280 (£213).
The US computer emergency readiness team said it "discourages individuals and organisations from paying the ransom, as this does not guarantee that access will be restored".
Eset has said that the malware was distributed via a bogus Adobe Flash update.
Bitfenders preliminary analysis reveals that this new strain of ransomware comes bundled with several open source tools that are leveraged for data encryption and lateral movement. The infection process starts with a fake Adobe Flash installer that is downloaded from compromised websites. This fake Flash installer holds the actual ransomware payload in a ZLIB-packed overlay. Once decrypted, it drops and executes the actual ransomware.
Bad Rabbit is extremely similar with GoldenEye / NotPetya both structurally and as broader focus; NotPetya took down many Ukrainian government agencies and businesses. It then spread across corporate networks of multinationals with operations or suppliers in eastern Europe.